This is a segment of the Supply Shock Newsletter. Subscribe to read the full edition.
How do you spend your time winning the lottery?
A new home, maybe a car. At least a warm summer holiday to sunny beaches.
However, I think it’s low on the list to use it to attack Bitcoin.
Well, 10 years ago, someone just burned good money.
This day: 2015
You already know that the debate over transaction filtering has been going on for years. Over 10 years.
Around this time in 2015, a mysterious user, or a group of users, decided to put the problem into their own hands.
The entity that coinwallet.eu progressed was beginning to run what is described as the “ultimate Bitcoin stress test.” They systematically spammed the chains with dust transactions, filling each block full, driving high through the sky in the process, significantly increasing the latency of legitimate users.
Coinwallet.eu demonstrated that Bitcoin’s 1MB block size limit was too small and wanted to convince the community to raise it in the end. After all, if spammers can overload their bitcoin blocks cheaply, others can do so at any time.
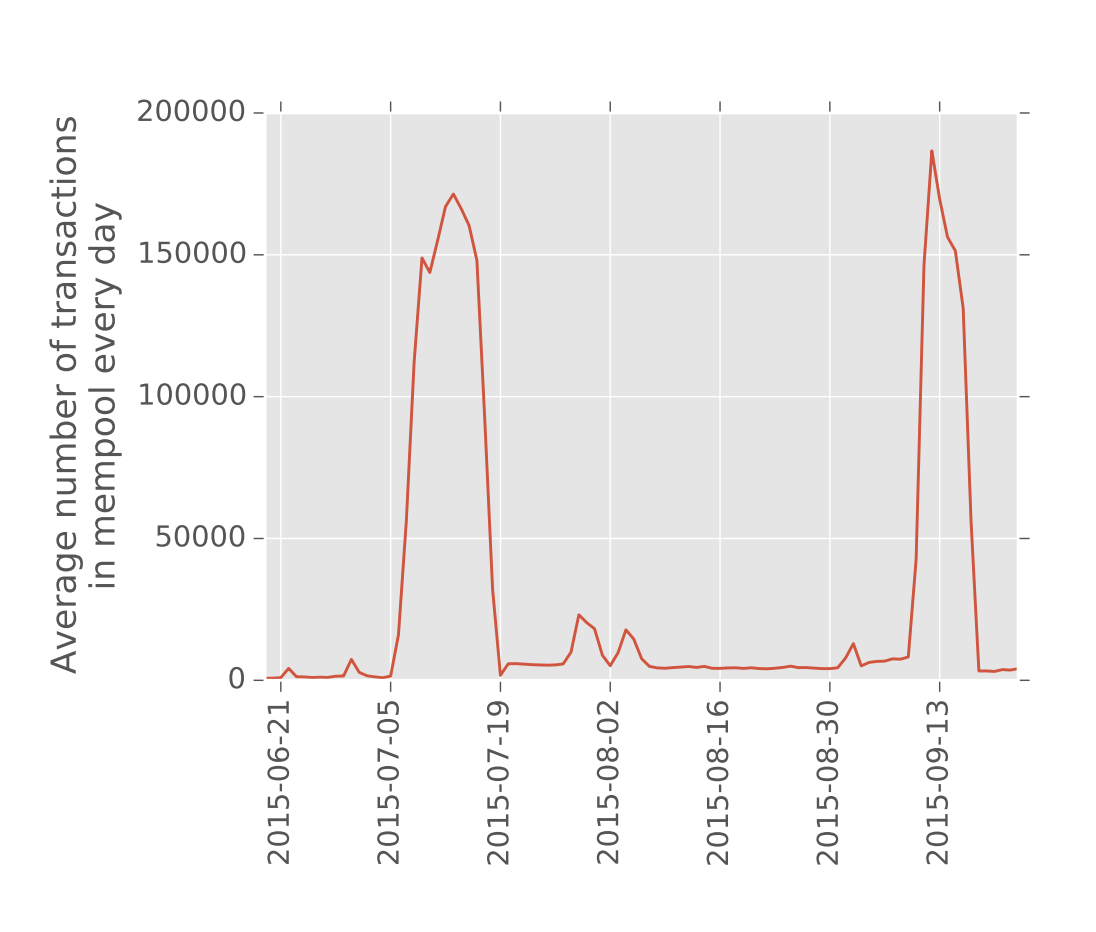 This campaign has caused chaos on the network, with the line showing the number of unconfirmed transactions. (sauce))
This campaign has caused chaos on the network, with the line showing the number of unconfirmed transactions. (sauce))
In a recent blog post, Bitmex Research wrote:
“The logic was that filling an 8MB block with spam would cost much more than filling a 1MB block. The small blocker retort in this argument was that if a larger blocker had spam, it would be quickly sorted out and cheaply not stopping spammers.”
“And if the block size limit increases, the fees will drop and the spam will be cheaper, but the key metric for big blockers was that filling blocks would cost a fee.
Coinwallet.eu campaigned in four attacks from June to September 2015.
At first it actually failed. It generates 1MB of transaction data every 5 minutes, causing a backlog of 241 blocks (1.67 days) of transactions. Mempool includes 241MB of unconfirmed transactions up to that point.
But after spending two BTCs ($500 at the time, $235,800), the server started crashing with just 12MB of member weight.
The second came five days later, and was even more effective and able to convince one user that there was a point on a big blocker.
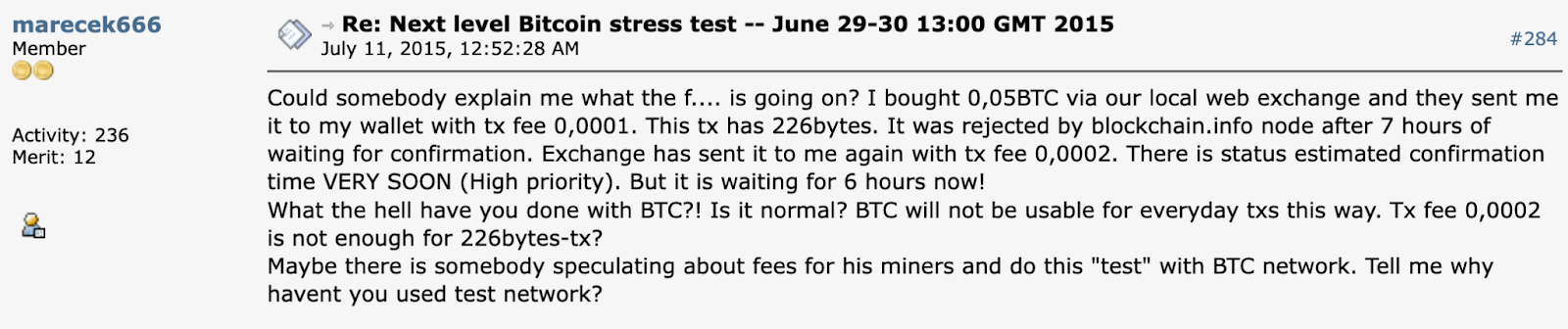 Marecek666 was not satisfied with the spam campaign.
Marecek666 was not satisfied with the spam campaign.
Coinwallet.eu was not expressly responsible for the third wave, but it is assumed that the group is responsible.
The attacks from July 7th to 11th resulted in a backlog of 27,000 to 80,000 transactions, sending many dust transactions (0.00001 BTC) to well-known wallets such as Wikileak and boats, and general public key addresses generated from simple key phrases such as “cats” and “dogs.”
The motherboard calculated that a total attacker spent 30 btc on its third wave network, worth $8,000, and now more than $3.5 million. When I undo the backlog, F2Pool had to consolidate most of the spam output in many 1MB transactions.
Coinwallet.eu’s fourth attack came in September with thousands of private keys posted to bitcointalk, each arriving with addresses containing 200 btc slices.
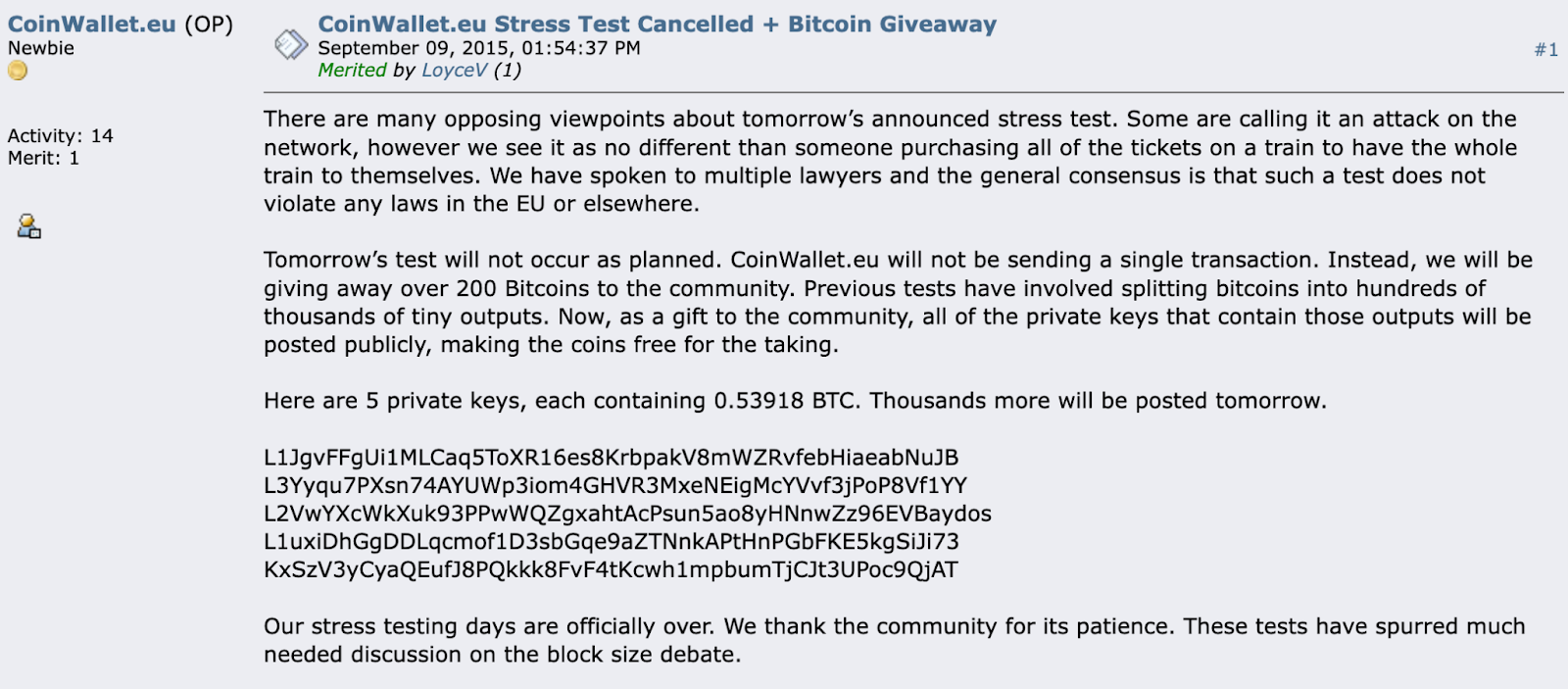
The user hastily collected free coins and submitted 90,000 transactions. Many of them are associated with the same Bitcoin, which can easily be discarded by miners and reduce the effectiveness of the attack.
Coinwallet.eu then gave up on the actions of miners, pools and key players, including Gregory Maxwell, to alleviate the adverse effects for a sufficient amount of time.
As Bitmex pointed out, the situation rhymes closely with modern discussions about the role of node runners to rule out certain types of transactions, at which point Luke Dashjr is driving the widespread use of filters to suppress spam in Coinwallet.eu.
It is still unknown who was behind Coinwallet.eu, with theories like Gerald Cotten and Big Blocker Craig Wright. In any case, academic research concluded that less than a quarter of the campaign’s peak 10-day transactions are spam (385,256 out of 1.65 million). Prices increased by 51% (45-68 SAT/BYTE), and processing delays increased to seven times (approximately 20 minutes to 2 hours and 45 minutes).






